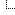10-19-2023, 09:07 AM
Ovo nije ništa novo samo sam ga upecao dok je sve još uvek online pa da podelim...
Mejl izgleda ovako:
Headeri, kontam da je hakovan nalog mada ovaj txreipartners.com nema ni sajt a i hostovan je u hrvatskoj, malo sus
Link u mejlu vodi ka pub-0691f791e27445e186a96f6163534e0a.r2 .dev/index.html#[email protected]
Stranica izgleda ovako:
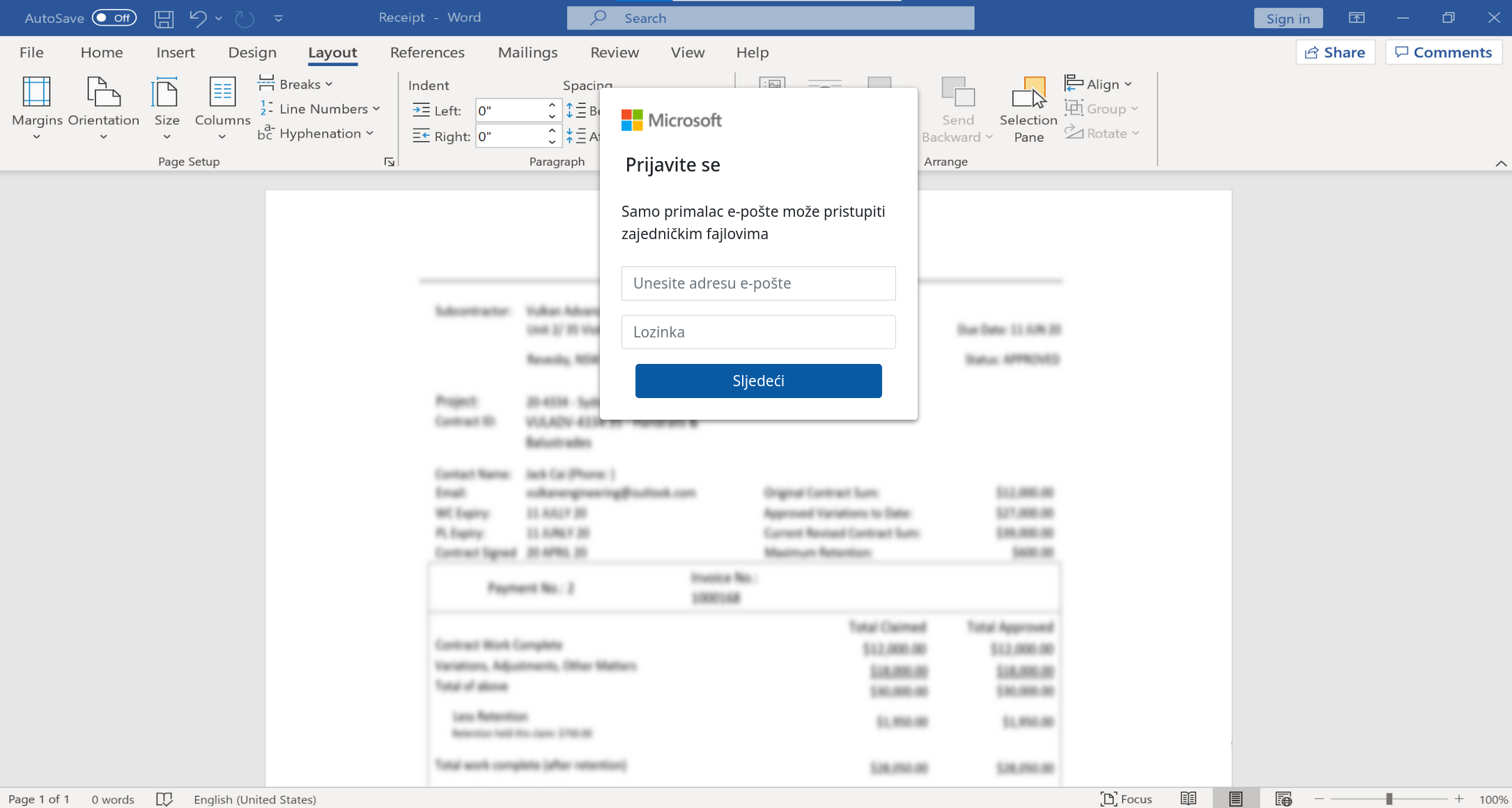
Kad se unese šifra pošalje je na mnemonicparsingbackup .xyz/ugovor/billions.php
Ovo ime foldera "ugovor" malo sus takođe, da nisu neki domaći ili regionalni akteri? Ili je samo hakovan hosting i taj folder se našao otvorenim, ne znam.
shared hostovan i registrovan na namecheap, možda od strane samih likova, mada je Creation Date: 2022-05-17T13:32:14.0Z
Pošto radi directory listing vidi se ovo:
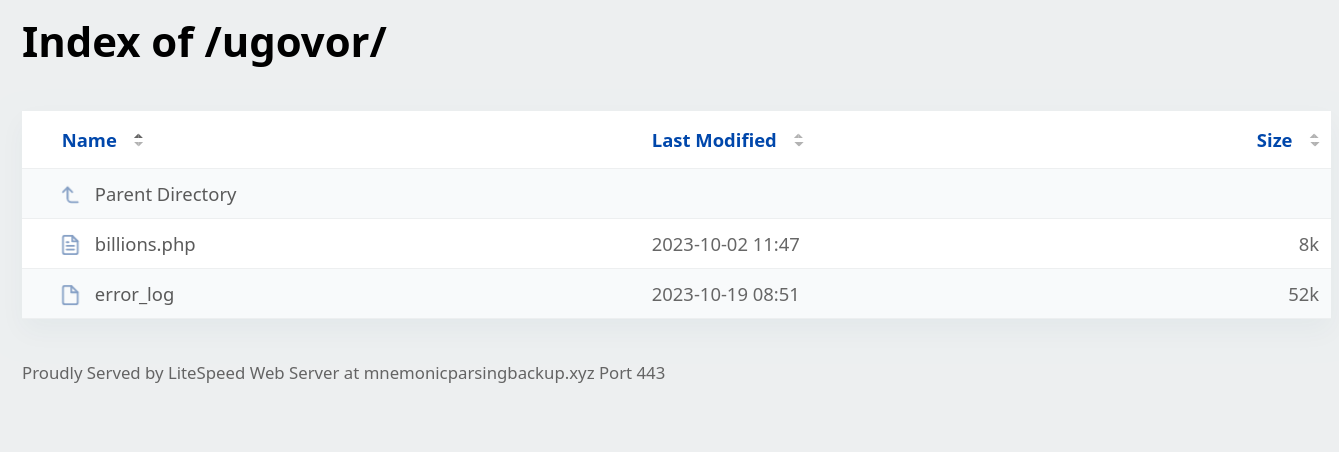
dobijam access denied za pristup error_log, u ovom fajlu su verovatno pokradene šifre i po veličini bih rekao da se dosta ljudi upeca na ovo
Mejl izgleda ovako:
Headeri, kontam da je hakovan nalog mada ovaj txreipartners.com nema ni sajt a i hostovan je u hrvatskoj, malo sus
Code:
txreipartners.com has address 88.209.205.83
txreipartners.com mail is handled by 1 txreipartners.com.Code:
Return-Path: <[email protected]>
Delivered-To: [email protected]
Received: from cp11.ulimitserver.com
by cp11.ulimitserver.com with LMTP
id L0S0HvsnLWWCWQAAEIIGUw
(envelope-from <[email protected]>)
for <[email protected]>; Mon, 16 Oct 2023 14:09:31 +0200
Return-path: <[email protected]>
Envelope-to: [email protected]
Delivery-date: Mon, 16 Oct 2023 14:09:31 +0200
Received: from chord.txreipartners.com ([88.209.205.83]:33034)
by cp11.ulimitserver.com with esmtps (TLS1.2) tls TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
(Exim 4.96.1)
(envelope-from <[email protected]>)
id 1qsMPK-0005sI-1U
for [email protected];
Mon, 16 Oct 2023 14:09:23 +0200
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=dkim; d=txreipartners.com;
h=From:To:Subject:Date:Message-ID:MIME-Version:Content-Type:Content-Transfer-Encoding; [email protected];
bh=6cKYkC+xJKS/zcHJg1C88Uwpwf0=;
b=FsSol1XJbaXiMd/fTETBxlRjC5DOOXnyjEDhwtb8RCquDCQLV8Cl1/4gWklFK+rKoTeBT+3XiTC+
MKgaiEvK0VCsZWQCTox0dCxkG/4sMWCbL/rwBGW963KrxHdJVyxUFhBx8lQ1r5TF3SfanN0kRMbl
yDG9XVTnfwI11nPjpjNRUzjLjGIH+Zh9c0DGyjlQ+hoFBpIIs6H8qoRdzfbryjYCNqI6Hvv5nixG
/d/juj1Ed1RR4qLIaLjn2ItLdKTjdgtPuUUkAfMk/suqdyZAmcwMUyc3YOpr8x8THPOOzl8jDD2N
KHFf86SNTxpjpgSM2/dlsIxeyPdmmoXqir9WyQ==
DomainKey-Signature: a=rsa-sha1; c=nofws; q=dns; s=dkim; d=txreipartners.com;
b=MXVGItK5Y63h1UUChGsvI72Ak0kDQVpqiC1QSjgoYr2uPmaOA9Ll6Q3HXsntZGqbHY02hmYQ5CnJ
qDvTHjtCMW1CTwpCRLclUu7b90jzBQl/ioPXLGeurw8KSQudoK8ea5x/4JtwSuwt2Hui7G0fvMJL
1vNHYztic1plgDcewWHfduUKGcjZDN7q/gTsaX7NcHs4pK2THwI1JoP44L7LAX3v7HygSswiEpKF
/9I33D8WwOyakfMoED52LSOLXliTkdZGRDZMiJz1MVyVM6rVxsUiwhG4tPyIUAf/oTJSi0uYIkwN
zMVWAeHTBuxNeBLFZyFiPoIjehpJOGxRx4wqcg==;
From: Microsoft SharePoint - BLAH.rs <[email protected]>
To: [email protected]
Subject: {Spam?} [email protected]
Date: 16 Oct 2023 05:09:13 -0700
Message-ID: <[email protected]>
MIME-Version: 1.0
Content-Type: text/html;
charset="iso-8859-1"
Content-Transfer-Encoding: quoted-printable
X-Spam-Subject: ***SPAM*** [email protected]
X-Spam-Status: Yes, score=9.2
X-Spam-Score: 92
X-Spam-Bar: +++++++++
X-Spam-Report: Spam detection software, running on the system "cp11.ulimitserver.com",
has identified this incoming email as possible spam. The original
message has been attached to this so you can view it or label
similar future email. If you have any questions, see
root\@localhost for details.
Content preview: Microsoft SharePoint Šifrovani dokumenti Imate šifrovane
dokumente iz Microsoft SharePoint-a Dokument 1: Ugovor Dokument 2: SWIFT
Dokument 3: Proforma faktura Iz sigurnosnih razloga, ovi dokumenti su šifrirani.
Pregledati Dokumente Hvala, Tim za Microsoft nalog
Content analysis details: (9.2 points, 5.0 required)
pts rule name description
---- ---------------------- --------------------------------------------------
2.5 URIBL_DBL_MALWARE Contains a malware URL listed in the Spamhaus
DBL blocklist
[URIs: txreipartners.com]
0.1 URIBL_CSS_A Contains URL's A record listed in the Spamhaus CSS
blocklist
[URIs: txreipartners.com]
-0.0 SPF_PASS SPF: sender matches SPF record
0.1 URI_HEX URI: URI hostname has long hexadecimal sequence
0.0 HTML_MESSAGE BODY: HTML included in message
0.1 MIME_HTML_ONLY BODY: Message only has text/html MIME parts
0.1 DKIM_SIGNED Message has a DKIM or DK signature, not necessarily
valid
-0.1 DKIM_VALID_AU Message has a valid DKIM or DK signature from
author's domain
-0.1 DKIM_VALID Message has at least one valid DKIM or DK signature
1.1 DCC_CHECK Detected as bulk mail by DCC (dcc-servers.net)
1.7 RAZOR2_CHECK Listed in Razor2 (http://razor.sf.net/)
2.4 RAZOR2_CF_RANGE_51_100 Razor2 gives confidence level above 50%
[cf: 100]
0.6 HTML_MIME_NO_HTML_TAG HTML-only message, but there is no HTML
tag
0.5 FSL_BULK_SIG Bulk signature with no Unsubscribe
0.1 TO_IN_SUBJ To address is in Subject
X-Spam-Flag: YES
X-PlusHosting-MailScanner-Information: Please contact the ISP for more information
X-PlusHosting-MailScanner-ID: 1qsMPK-0005sI-1U
X-PlusHosting-MailScanner: Found to be clean
X-PlusHosting-MailScanner-SpamCheck: spam, SpamAssassin (not cached,
score=8.965, required 5, DCC_CHECK 1.10, DKIM_SIGNED 0.10,
DKIM_VALID -0.10, DKIM_VALID_AU -0.10, DKIM_VALID_EF -0.10,
FSL_BULK_SIG 0.47, HTML_MESSAGE 0.00, HTML_MIME_NO_HTML_TAG 0.64,
MIME_HTML_ONLY 0.10, RAZOR2_CF_RANGE_51_100 2.43, RAZOR2_CHECK 1.73,
SPF_PASS -0.00, URIBL_CSS_A 0.10, URIBL_DBL_MALWARE 2.50,
URI_HEX 0.10)
X-PlusHosting-MailScanner-SpamScore: ssssssss
X-PlusHosting-MailScanner-From: [email protected]Link u mejlu vodi ka pub-0691f791e27445e186a96f6163534e0a.r2 .dev/index.html#[email protected]
Stranica izgleda ovako:
Kad se unese šifra pošalje je na mnemonicparsingbackup .xyz/ugovor/billions.php
Ovo ime foldera "ugovor" malo sus takođe, da nisu neki domaći ili regionalni akteri? Ili je samo hakovan hosting i taj folder se našao otvorenim, ne znam.
shared hostovan i registrovan na namecheap, možda od strane samih likova, mada je Creation Date: 2022-05-17T13:32:14.0Z
Pošto radi directory listing vidi se ovo:
dobijam access denied za pristup error_log, u ovom fajlu su verovatno pokradene šifre i po veličini bih rekao da se dosta ljudi upeca na ovo