Jutros vidim na linkedinu ovu objavu:
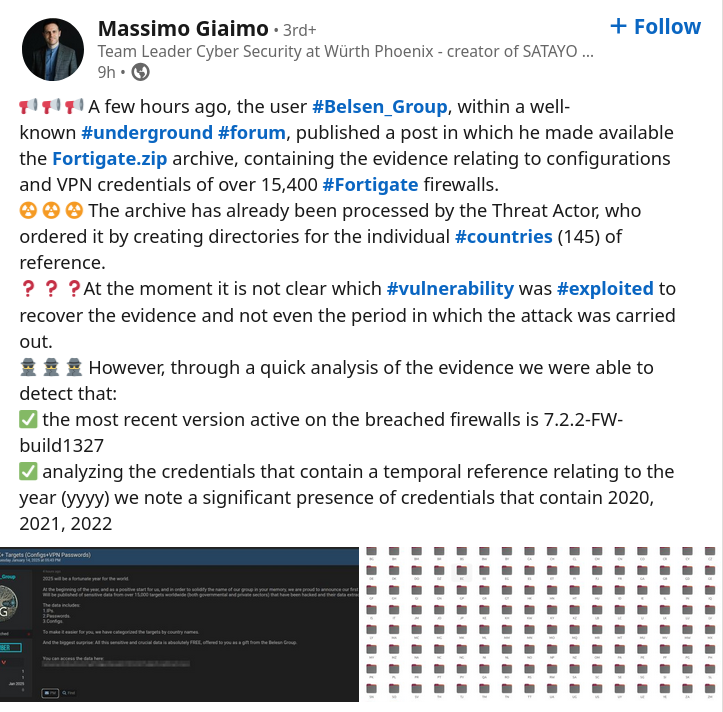
Dakle neki maliciozan je preko nepoznatog propusta pokupio konfiguracije i VPN šifre sa 15,400 Fortigate firewalla po celom svetu i objavio za besplatno skidanje. Po ovoj objavi deluje da su malo stariji podaci u pitanju.
Maliciozni akter nudi podatke potpuno besplatno, može se računati da trenutno razni drugi pokušavaju da iskoriste ove podatke...

Ako koristite Fortigate uređaje na ivici mreže iz predostrožnosti ODMAH promenite sve šifre... administratorske, VPN šifre pod obavezno, WiFi šifre su takođe u konfig fajlovima tako da bolje i njih. Jeste da su šifre SHA256 hešovane ali bolje promeniti
Od Ex-yu zemalja među konfiguracijama prisutni su i u zagradama koliko puta uključujući i duplikate jer ih ima : BA (47) MK (2) RS (31) SI (13)
Podeliću zanimljivosti za Srbiju...
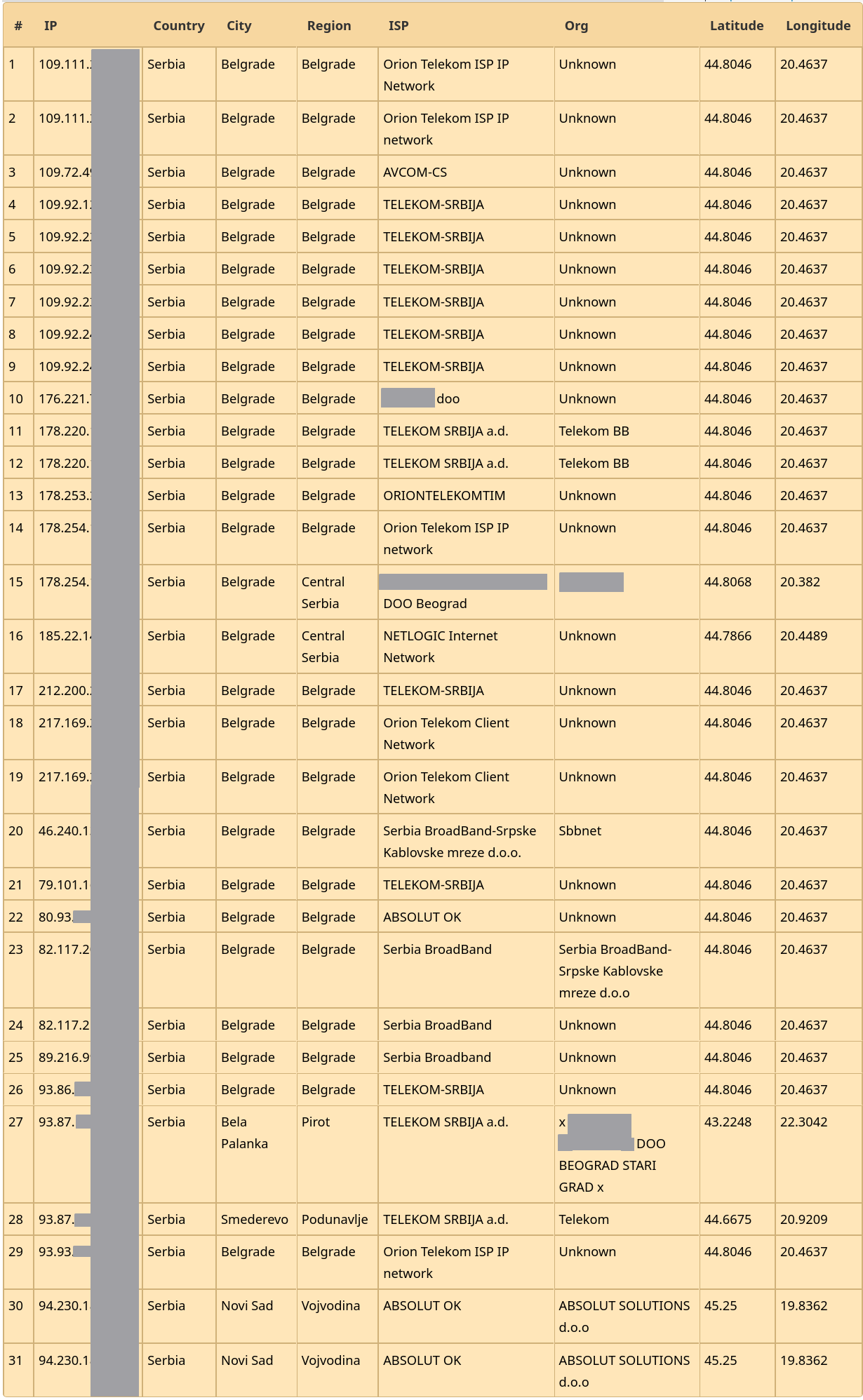
Zastupljene IP adrese tj. provajderi. Nemojte se osećati lagodno ako vam se IP adresa menja, u konfiguracijama je konfigurisan DDNS i svako ko ima fajl može da dođe do trenutne IP adrese vašeg rutera...
Zastupljeni uređaji i verzije:
Zbog osetljivosti i rizika neću spominjati imena korisnika rutera ali moram da napravim neka zapažanja među podacima:
Razumem ja da je potrebno dostaviti klijentu početne šifre, to i sam redovno radim, ali valjda mogu i one biti sigurne, jer kao što je opšte poznato korisnici neće promeniti šifre ako ne moraju. Da ne bude da samo kritikujem, ima i onih sa dobrim šiframa koje se na primer kod jednog rutera sastoje od 9 random karaktera malih i velikih slova kao i broje, jedinstvenih za svakog korisnika.
Dakle neki maliciozan je preko nepoznatog propusta pokupio konfiguracije i VPN šifre sa 15,400 Fortigate firewalla po celom svetu i objavio za besplatno skidanje. Po ovoj objavi deluje da su malo stariji podaci u pitanju.
Maliciozni akter nudi podatke potpuno besplatno, može se računati da trenutno razni drugi pokušavaju da iskoriste ove podatke...
Ako koristite Fortigate uređaje na ivici mreže iz predostrožnosti ODMAH promenite sve šifre... administratorske, VPN šifre pod obavezno, WiFi šifre su takođe u konfig fajlovima tako da bolje i njih. Jeste da su šifre SHA256 hešovane ali bolje promeniti
Od Ex-yu zemalja među konfiguracijama prisutni su i u zagradama koliko puta uključujući i duplikate jer ih ima : BA (47) MK (2) RS (31) SI (13)
Podeliću zanimljivosti za Srbiju...
Zastupljene IP adrese tj. provajderi. Nemojte se osećati lagodno ako vam se IP adresa menja, u konfiguracijama je konfigurisan DDNS i svako ko ima fajl može da dođe do trenutne IP adrese vašeg rutera...
Zastupljeni uređaji i verzije:
Code:
FG200E-7.0.2-FW-build0234-211019:opmode=0:vdom=0:user=Local_Process_Access
FGT80F-7.0.5-FW-build0304-220208:opmode=0:vdom=0:user=Local_Process_Access
FGT40F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FGT60F-7.2.1-FW-build1254-220803:opmode=0:vdom=0:user=Local_Process_Access
FGT60F-7.2.1-FW-build1254-220803:opmode=0:vdom=0:user=Local_Process_Access
FG200E-7.0.2-FW-build0234-211019:opmode=0:vdom=0:user=Local_Process_Access
FGT80F-7.0.6-FW-build0366-220606:opmode=0:vdom=0:user=Local_Process_Access
FG100F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FGT80F-7.0.5-FW-build0304-220208:opmode=0:vdom=0:user=Local_Process_Access
FGT80F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FGT80F-7.2.1-FW-build1254-220803:opmode=0:vdom=0:user=Local_Process_Access
FGT40F-7.2.1-FW-build1254-220803:opmode=0:vdom=0:user=Local_Process_Access
FGT60F-7.0.1-FW-build0157-210714:opmode=0:vdom=0:user=Local_Process_Access
FGT60E-7.2.0-FW-build1157-220331:opmode=0:vdom=1:user=Local_Process_Access
FGT40F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FG100F-7.2.1-FW-build1254-220803:opmode=0:vdom=1:user=Local_Process_Access
FG100E-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FGT61F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FGT40F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FG100E-7.0.1-FW-build0157-210714:opmode=0:vdom=0:user=Local_Process_Access
FG80FP-7.2.1-FW-build1254-220803:opmode=0:vdom=0:user=Local_Process_Access
FG100F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FG100F-7.0.5-FW-build0304-220208:opmode=0:vdom=0:user=Local_Process_Access
FGT40F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FGT60F-7.0.1-FW-build0157-210714:opmode=0:vdom=0:user=Local_Process_Access
FG100F-7.0.5-FW-build0304-220208:opmode=0:vdom=0:user=Local_Process_Access
FG200F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FGT40F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_Access
FGT61F-7.2.1-FW-build1254-220803:opmode=0:vdom=0:user=Local_Process_Access
FGT60E-7.0.3-FW-build0237-211207:opmode=0:vdom=0:user=Local_Process_Access
FG100F-7.2.0-FW-build1157-220331:opmode=0:vdom=0:user=Local_Process_AccessZbog osetljivosti i rizika neću spominjati imena korisnika rutera ali moram da napravim neka zapažanja među podacima:
- Ruter koji pripada firmi koja proizvodi i prodaje peciva. Među VPN šiframa na čak 4 naloga je šifra "Comtrade123#". Te pretpostavljam da im je Comtrade radio mrežu, veoma neodgovorno postavljanje šifara.
- Ruter od jedne outsourcing IT firme iz Beograda, čak 8 VPN naloga sa korisničkim imenima lakih za pogađanje imao je šifru "stacemodajedemo"
- Ruter od jedne sportske organizacije u Beogradu, korisnička imena su "Ime" a šifre su sve "123Ime456"
- Firma iz Novog Sada koja nudi usluge vođenja poslovanja i u sklopu toga nudi i Fortinet uređaje, među VPN šiframa su "stagod1, stagod2, stagod3" itd, kao i šifre "vpnsifra123, vpnsifra321, sifrazavpn123...". A i ostale šifre su podjednako loše.
- Jedna medicinska laboratorija sa gomilom ispostava po celoj Srbiji... VPN šifre izuzetno loše, ističe se kao šifra "L031nka"
Razumem ja da je potrebno dostaviti klijentu početne šifre, to i sam redovno radim, ali valjda mogu i one biti sigurne, jer kao što je opšte poznato korisnici neće promeniti šifre ako ne moraju. Da ne bude da samo kritikujem, ima i onih sa dobrim šiframa koje se na primer kod jednog rutera sastoje od 9 random karaktera malih i velikih slova kao i broje, jedinstvenih za svakog korisnika.