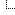Posts: 1,056
Threads: 405
Joined: Sep 2022
Reputation:
308
 05-31-2024, 10:03 PM
(This post was last modified: 05-31-2024, 11:15 PM by milos_rs.)
05-31-2024, 10:03 PM
(This post was last modified: 05-31-2024, 11:15 PM by milos_rs.)
Pun naziv firme: PODZEMNO SKLADIŠTE GASA BANATSKI DVOR DRUŠTVO SA OGRANIČENOM ODGOVORNOŠĆU NOVI SAD
Nema nezavisne potvrde o događaju, ali veoma je verovatan videvši da je postojalo dobro predosećanje: Na prodaju VPN pristup za srpsko transportno-skladišno preduzeće
Glavna vest: RansomHub Cyberattack Targets Serbian Gas Firm PSG BANATSKI DVOR, Disables SCADA Systems
Quote:According to the threat actor post, the RansomHub exfiltrated a substantial amount of data totaling 80 GB. Among the stolen information are critical files encompassing IT, Accounting, Finance, Projects, Client database (in SQL format), Budgets, Taxes, Logistics and supply chain management, Production data, HR, Legal data, KPI, and R&D documents.
Additionally, the threat actors has allegedly disabled the SCADA (Supervisory Control and Data Acquisition) systems, further exacerbating the operational impact of the attack.
The cybercriminals have set a deadline of 5 days for the potential leak of the stolen data, adding urgency to the situation. The implications of such a breach extend beyond PSG BANATSKI DVOR, affecting not only the company but also its clients and stakeholders.
Moreover, the PSG BANATSKI DVOR website is currently nonfunctional and is displaying a “took too long to respond” error. This error, often associated with cyberattacks, suggests disruptions in the normal functioning of the website, possibly due to overwhelming server loads or exploitation of vulnerabilities in the site’s infrastructure.
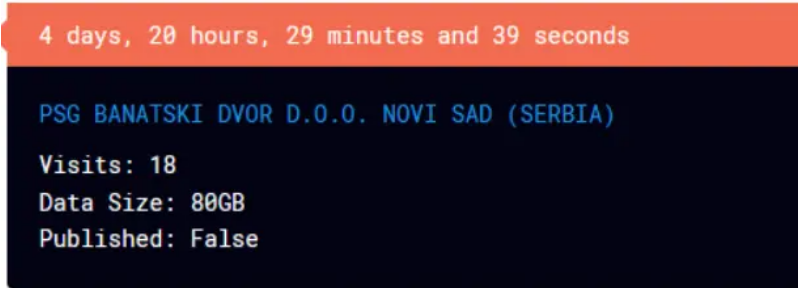 Threat Actor Blames Employee for the PSG BANATSKI DVOR Cyberattack
Threat Actor Blames Employee for the PSG BANATSKI DVOR Cyberattack
Quote:“We have all the important files, such as: IT, Accounting, Finance, Projects, Client database (in SQL format) Budgets, Taxes, Logistics and supply chain management, Production data, HR, Legal data, KPI, R&D. Over 80 GB of sensational information has been downloaded”
Additionally, the group blames an employee named Dejan Belić for the breach. The threat actors have previously targeted similar victims and share similarities with traditional Russian ransomware groups while refraining from targeting certain countries and non-profits.
Posts: 1,056
Threads: 405
Joined: Sep 2022
Reputation:
308
05-31-2024, 10:18 PM
(This post was last modified: 06-01-2024, 07:01 AM by milos_rs.)
sa dark web sajta ransomware ekipe:
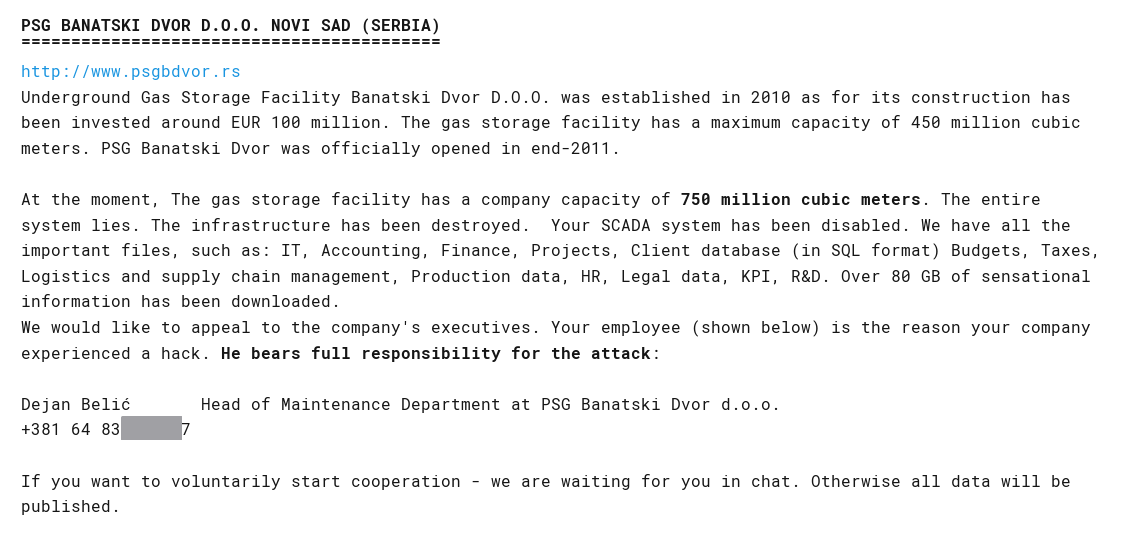
rok da se žrtva javi radi pregovora ističe u ponedeljak 03.06 u 14h
Posts: 1,056
Threads: 405
Joined: Sep 2022
Reputation:
308
05-31-2024, 11:06 PM
(This post was last modified: 06-01-2024, 06:58 AM by milos_rs.)
domeni firme:
psgbdvor.rs
psgbdvor.com
psgbdvor.net
svi idu na:
Code: psgbdvor.rs has address 194.247.196.19
psgbdvor.rs mail is handled by 10 mail.psgbdvor.rs.
psgbdvor.rs mail is handled by 20 relay.eunet.rs.
mail.psgbdvor.rs has address 213.240.41.18
takođe postoji i ns.psgbdvor.rs kao i webmail.psgdbvor.rs koji takođe idu na adresu 213.240.41.18
SPF: v=spf1 ip4:213.240.41.18 ip4:213.240.41.24 ~all
194.247.196.19 je verovatno web hosting kod yunet.rs - YUNET INTERNATIONAL d.o.o.
Sajt na IP adresi kao i sama IP adresa su nedostupni, kada su poslednji put bili dostupni ne mogu da nađem, moguće je da nije nikada ni bio aktivan sajt jer ne nalazim ni jednu keširanu kopiju?
IP adresa gde je mejl server, 213.240.41.18, je deo koji je YUNET delegirao samoj firmi:
Code: inetnum: 213.240.41.16 - 213.240.41.31
netname: PSG-BANATSKIDVOR-NET
descr: PSG Banatski dvor d.o.o.
descr: Narodnog fronta 12
descr: 21000 Novi Sad
descr: Serbia
country: RS
admin-c: BV2061-RIPE
tech-c: DB18486-RIPE
status: ASSIGNED PA
mnt-by: AS8771-MNT
created: 2013-07-24T10:25:38Z
last-modified: 2013-07-24T10:25:38Z
source: RIPE # Filtered
person: Branislava Vukic
address: PSG Banatski dvor d.o.o.
address: Narodnog fronta 12
address: 21000 Novi Sad
address: Serbia
phone: +381 21 481 2115
fax-no: +381 21 471 4361
nic-hdl: BV2061-RIPE
mnt-by: AS8771-MNT
created: 2013-07-24T10:25:38Z
last-modified: 2013-07-24T10:25:38Z
source: RIPE # Filtered
person: Dejan Belic
address: PSG Banatski dvor d.o.o.
address: Narodnog fronta 12
address: 21000 Novi Sad
address: Serbia
phone: +381 21 481 2115
fax-no: +381 21 471 4361
nic-hdl: DB18486-RIPE
mnt-by: AS8771-MNT
created: 2013-07-24T10:25:38Z
last-modified: 2013-07-24T10:25:38Z
route: 194.247.192.0/19
descr: YUnet International
origin: AS8771
mnt-by: AS8771-MNT
created: 2002-08-20T20:37:38Z
last-modified: 2013-08-07T10:26:56Z
source: RIPE
Code: traceroute to 213.240.41.18 (213.240.41.18), 30 hops max, 60 byte packets
...
7 telekom.sox.rs (185.1.27.38) 8.415 ms 11.010 ms 11.000 ms
8 212.200.7.69 (212.200.7.69) 10.991 ms 9.533 ms 9.119 ms
9 durum.mitsidespoint.co.yu (212.200.231.206) 11.116 ms 11.103 ms 11.122 ms
10 mail.psgbdvor.rs (213.240.41.18) 10.728 ms 10.719 ms 11.063 ms^C
Mejl server je u ovom trenutku nedostupan. Sad zapravo nisam siguran da li je bio nedostupan jer kad sam išao da proverim još jednom radio je :

Takođe je zanimljivo da je do (možda) 2024-05-28 mail.psgbdvor.rs bio usmeren na drugu IP adresu, 92.42.254.113, koja je kod mediaworksit.net tj. Orion Telekom-a, mada da li se ovo zaista desilo i datum kada se desilo ne mogu da precizno odredim.
Timeline za sada:
2024-05-20 : Objavljuje se prodaja pristupa firmi - https://bezbedanbalkan.net/thread-1482.html
2024-05-28 : Ransomware grupa objavljuje da je kompromitovala firmu, istog dana se navodno menja DNS mejl servera sa IP adrese Orion-a na sopstvenu IP adresu. Dan kasnije je objavljena vest koja je linkovana u prvom komentaru ove teme, a prva spomen na X-u je datuma 2024-05-28 14:58
Posts: 1,056
Threads: 405
Joined: Sep 2022
Reputation:
308
Posts: 1,056
Threads: 405
Joined: Sep 2022
Reputation:
308
06-03-2024, 07:37 AM
(This post was last modified: 06-07-2024, 12:35 PM by milos_rs.)
izgleda da je rok za pregovore produžen, moguće je da su iz firme tražili više vremena
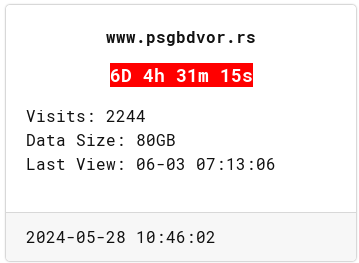
novi rok je 2024-06-09 u 14h
takođe na ovoj novoj stranici od ransomware ekipe vidimo da je prvobitno objavljivanje kompromitacije bilo 2024-05-28 u 10:46:02
Ova promena roka može da se smatra svojevrsnom potvrdom da je kompromitacija istinita i da je firma stupila u kontakt sa malicioznim akterima.
Ažuriran timeline:
2024-05-20 : Objavljuje se prodaja pristupa firmi - https://bezbedanbalkan.net/thread-1482.html
2024-05-28 : Ransomware grupa objavljuje u 10:46 da je kompromitovala firmu, rok za pregovore je 2024-06-03 u 14h. Istog dana se navodno menja DNS mejl servera sa IP adrese Orion-a na sopstvenu IP adresu. Dan kasnije je objavljena vest koja je linkovana u prvom komentaru ove teme, a prva spomen na X-u je datuma 2024-05-28 u 14:58
2024-06-03 (ili 02) : Ransomware grupa produžava vreme za pregovore na još otprilike nedelju dana, rok je sada 2024-06-09 u 12h
Posts: 1,056
Threads: 405
Joined: Sep 2022
Reputation:
308
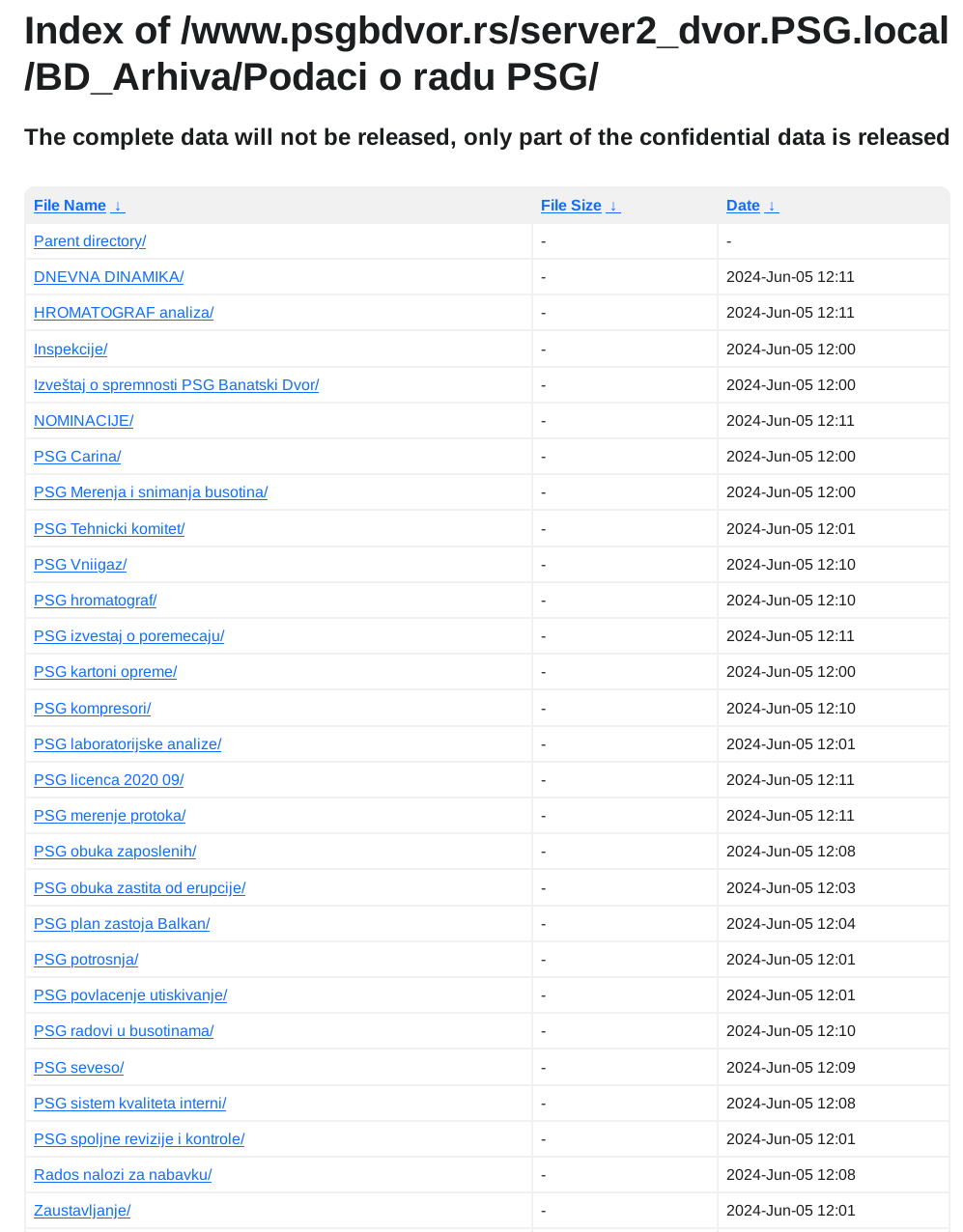
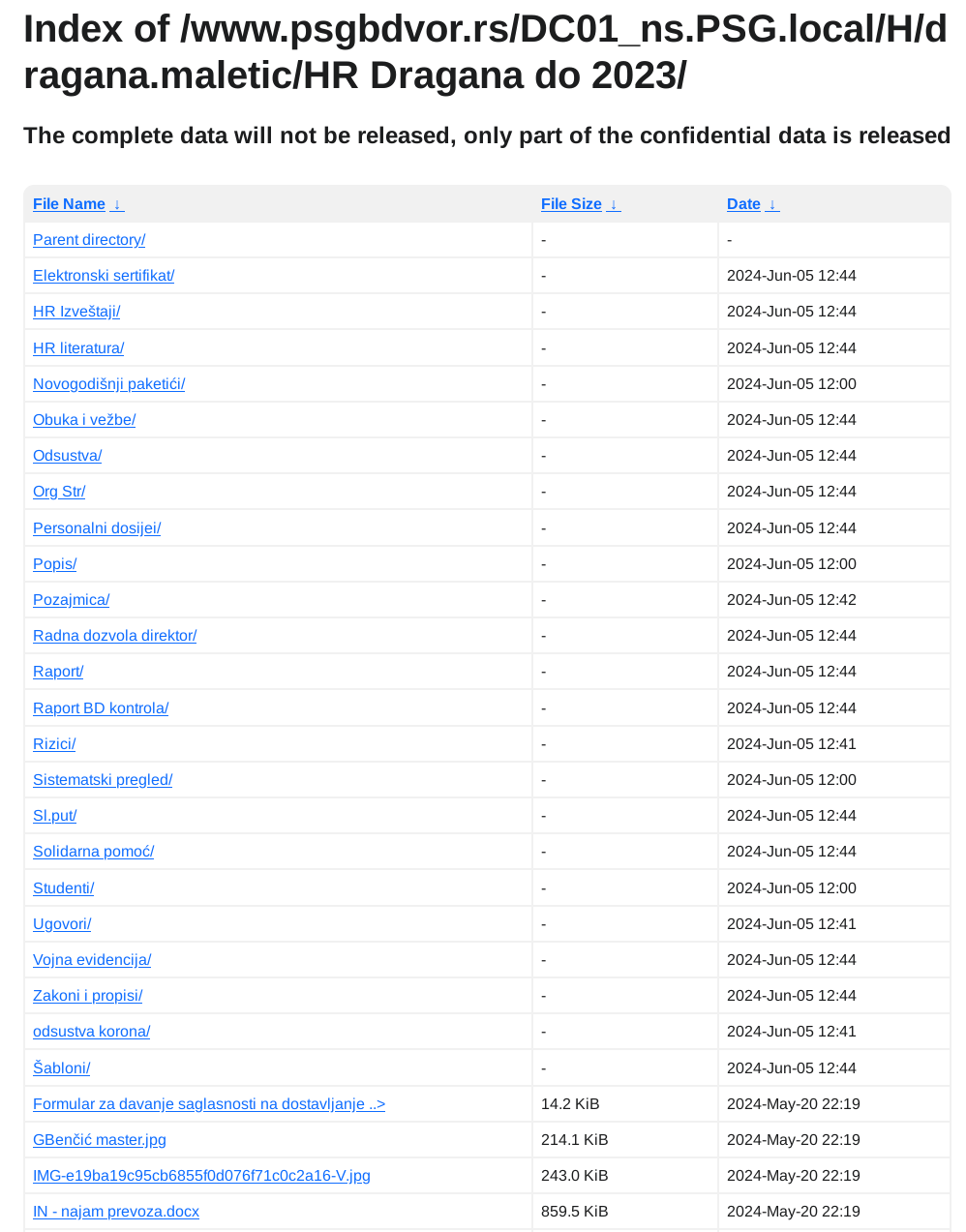
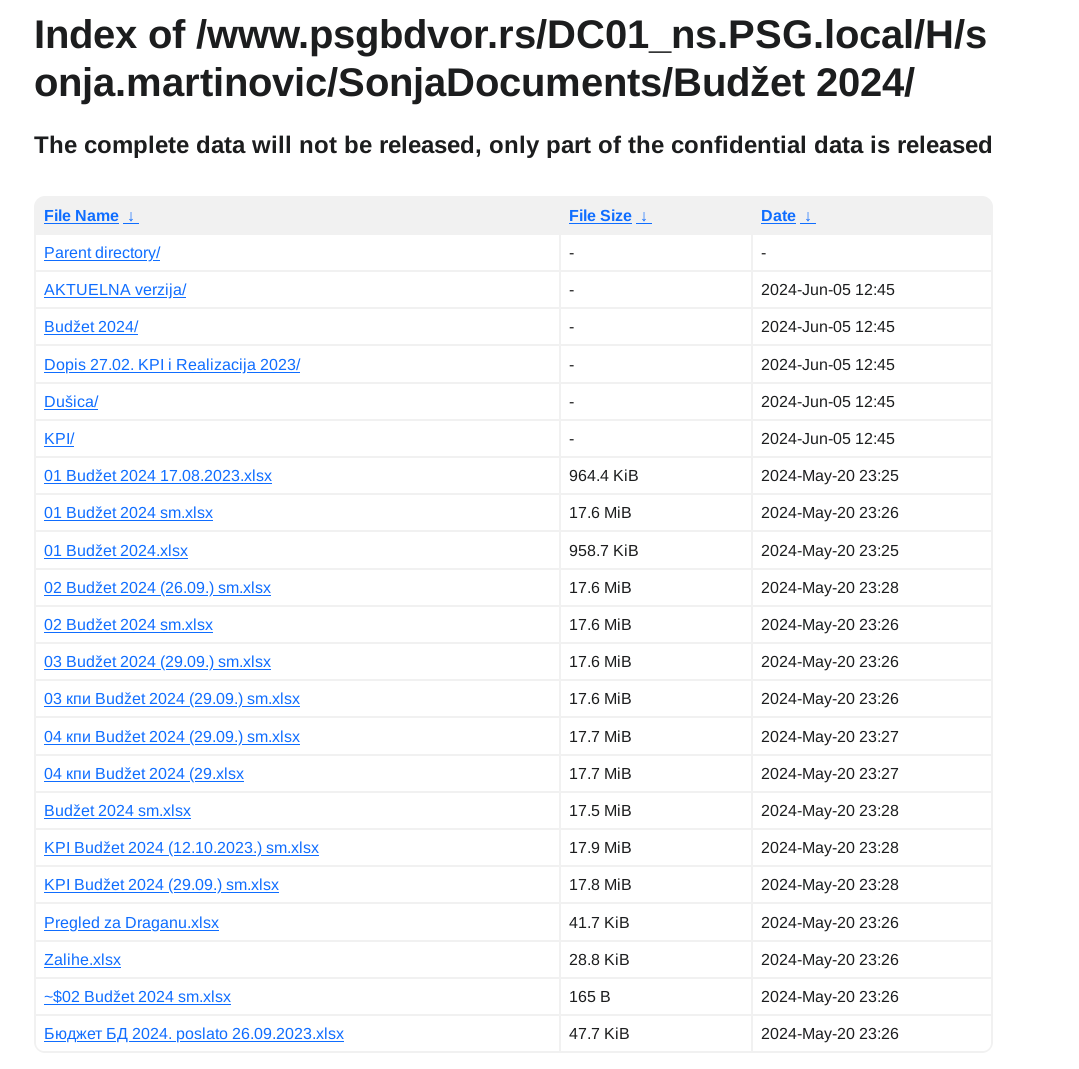
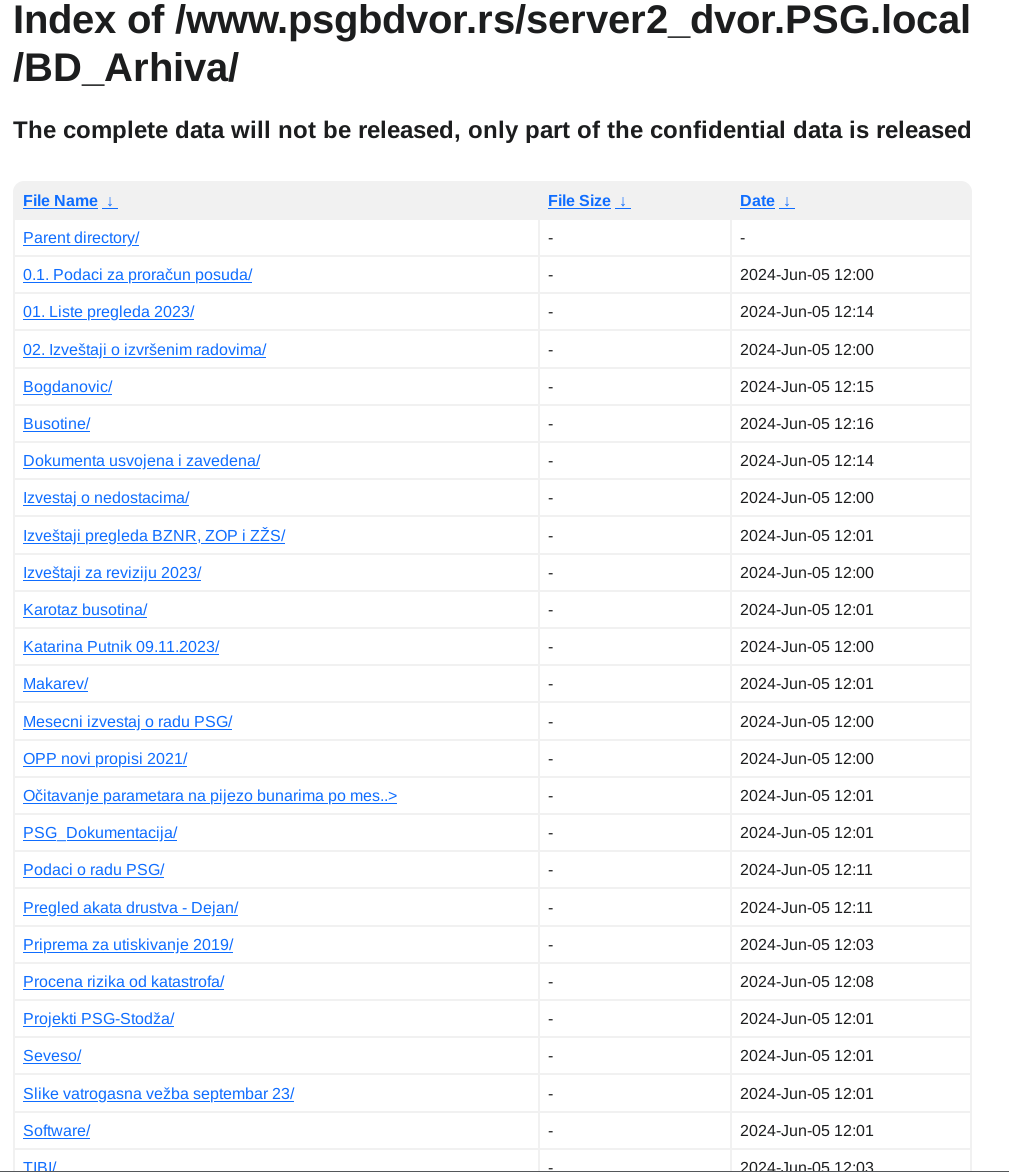
Podaci su objavljeni...
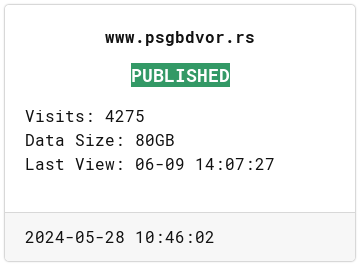
Ali piše "The complete data will not be released, only part of the confidential data is released". Koliko sam primetio ovo piše na svim objavljenim podacima ove ransomware grupe. Da li znači da je za deo podataka plaćen otkup, ili deo podataka ide na privatnu prodaju daljim malicioznim akterima, ili iz svoje dobrobiti ne objavljuju sve podatke... to nemam kako da znam.
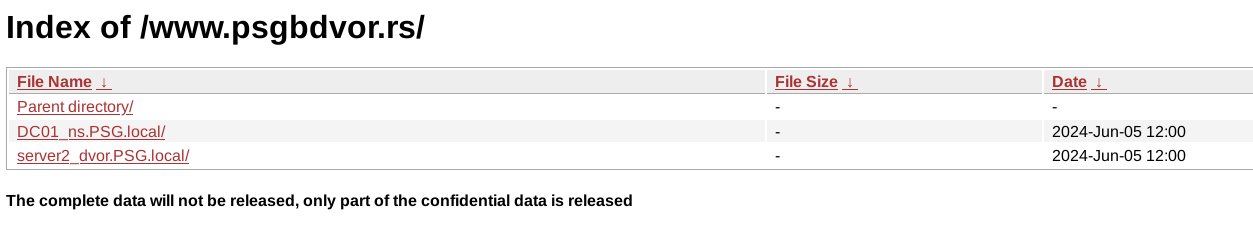
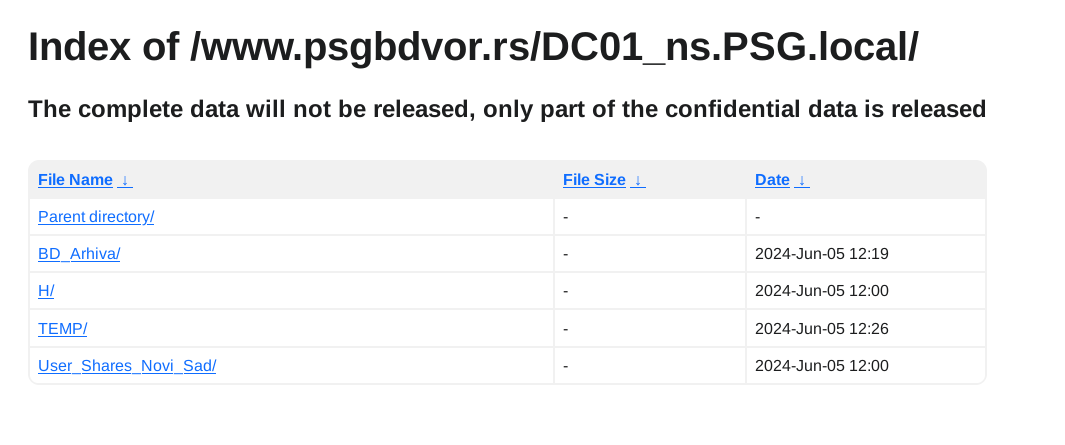
Iz objavljenih podataka se vidi da su maliciozni akteri imali pristup minimum dva servera po imenima DC01_ns.PSG.local i server2_dvor.PSG.local jedan od kojih je očigledno glavni domen kontroler. Kakav tačan pristup su imali ne mogu znati, ali verovatno administratorskog nivoa. U objavljenim podacima se nalaze file share-ovi koji su na ovim serverima, izgleda da im je DC ujedno bio i File Share server, što nije preporučljivo.
U podacima ima svašta, od kompletne HR dokumentacije uključujući rešenja, skenirane lične karte zaposlenih itd, do inventara IT uređaja kao i ostalih sredstava za rad, finansijski izveštaji i budžeti po godinama uključujući i 2024, razna rešenja, izveštaji, softverske licence, procene rizika, ne znam ni sam šta sve nema nit sam stručan nit me nešto preterano interesuje. Ostaviću pojedine skrinšote fajl strukture objavljenih fajlova da se stekne utisak:
Ovo što su maliciozni akteri okrivili Dejana Belića za propust, možda je jer je držao VPN šifre u Excel tabeli? :
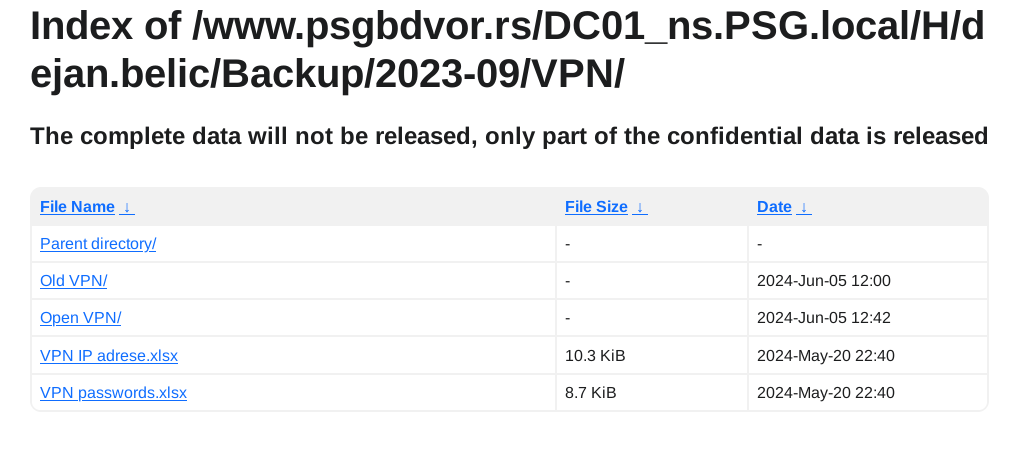
Primeri fajlova:
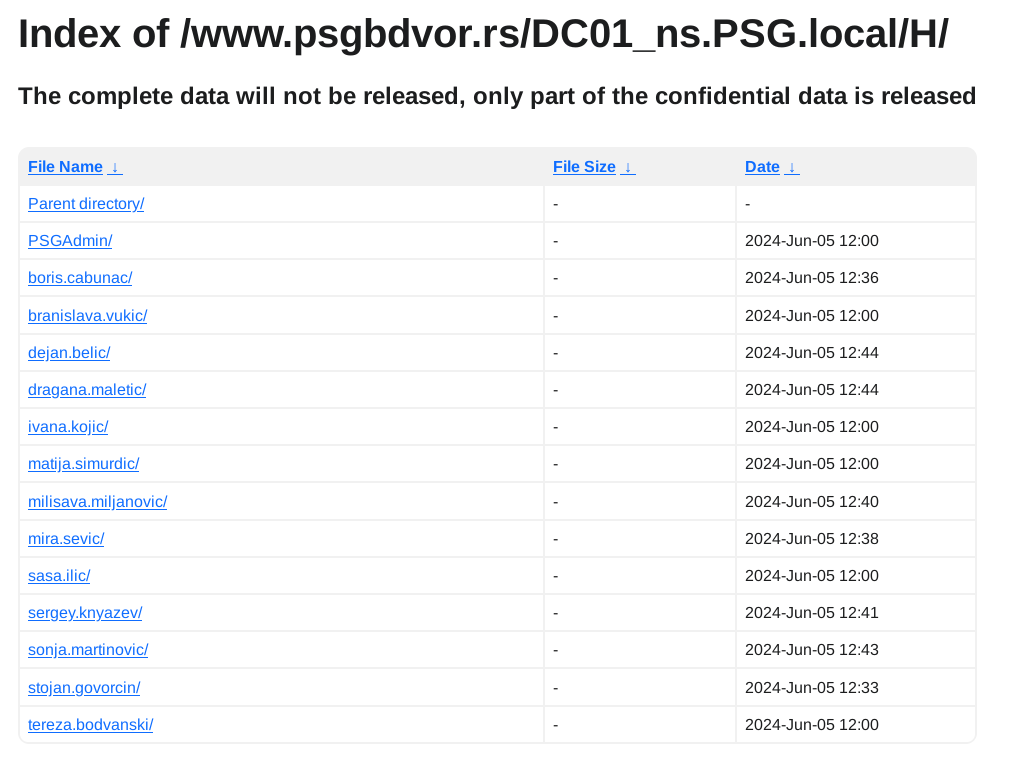
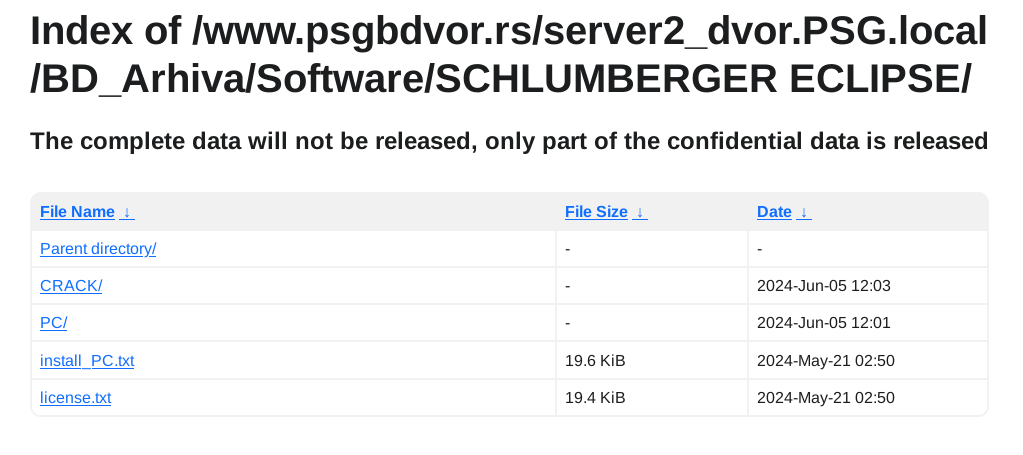
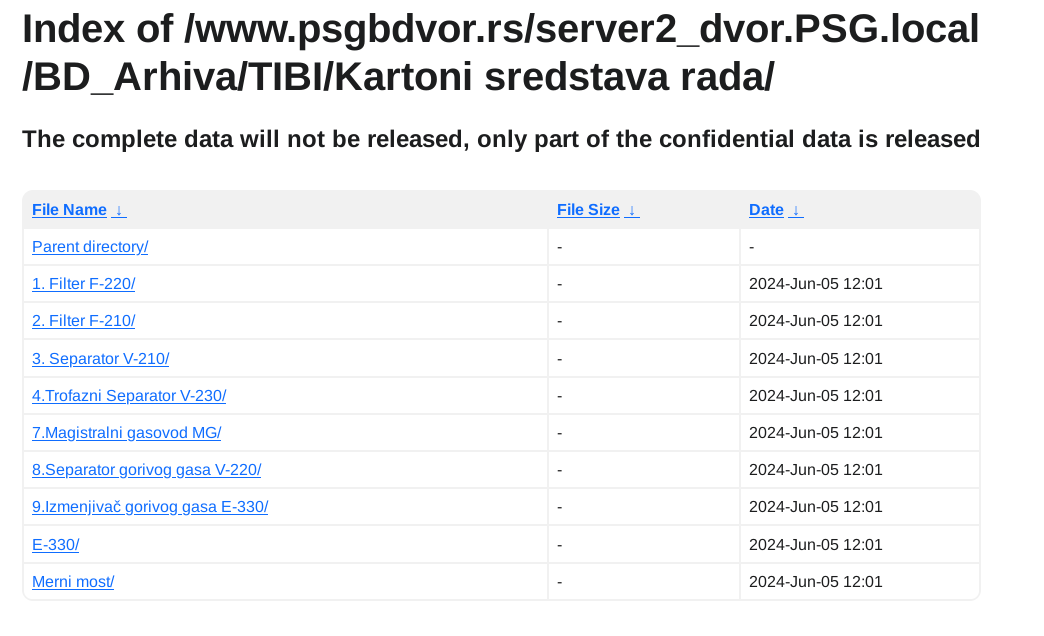
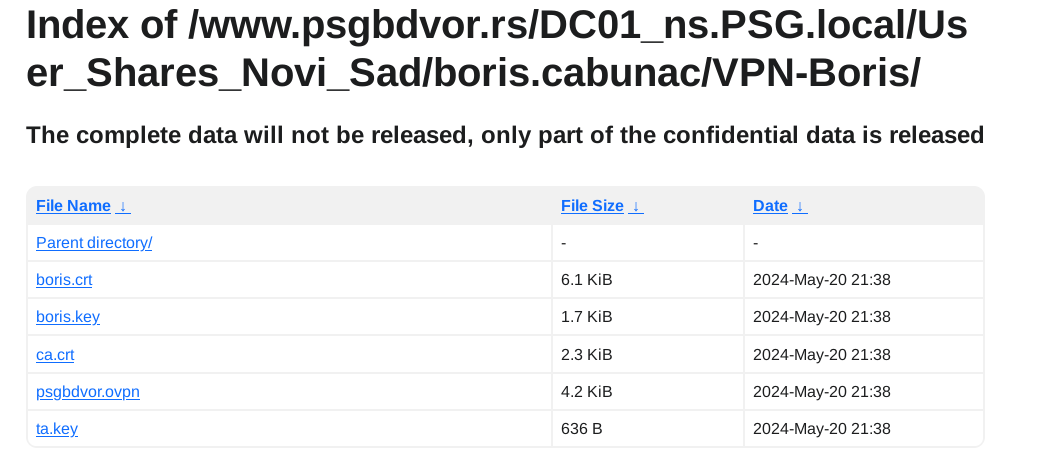

Posts: 793
Threads: 443
Joined: Oct 2023
Reputation:
162
Ransomware notes
readme_[id]_2.txt
Quote:Hello!
Visit our Blog:
Tor Browser Links:
http://ransomxifxwc5eteopdobynonjctkxxva...ecgbqdw6qd(.)onion/
Links for normal browser:
http://ransomxifxwc5eteopdobynonjctkxxva...ecgbqdw6qd.()onion(.)ly/
>>> Your data is stolen and encrypted.
If you don't pay the ransom, the data will be published on our TOR darknet sites. Keep in mind that once your data appears on our leak site, it could be bought by your competitors at any second, so don't hesitate for a long time. The sooner you pay the ransom, the sooner your company will be safe.
>>> If you have an external or cloud backup; what happens if you donâ t agree with us?
All countries have their own PDPL (Personal Data Protection Law) regulations. In the event that you do not agree with us, information pertaining to your companies and the data of your companyâ s customers will be published on the internet, and the respective countryâ s personal data usage authority will be informed. Moreover, confidential data related to your company will be shared with potential competitors through email and social media. You can be sure that you will incur damages far exceeding the amount we are requesting from you should you decide not to agree with us.
>>> How to contact with us?
- Install and run 'Tor Browser' from https://www.torproject.org/download/
- Go to http://cki3klxqycazagx3r5prae3nmfvxmwa34...vxd76akqid(.)onion/
- Log in using the Client ID: [snip]
>>> WARNING
DO NOT MODIFY ENCRYPTED FILES YOURSELF.
DO NOT USE THIRD PARTY SOFTWARE TO RESTORE YOUR DATA.
YOU MAY DAMAGE YOUR FILES, IT WILL RESULT IN PERMANENT DATA LOSS.
This link (TOR) is your private blog link. Right now it is only available to you but in 72 hours if you don't get in touch it will be published on our platform and will be seen by thousands of journalists: ransomxifxwc5eteopdobynonjctkxxvap77yqifu2emfbecgbqdw6qd(.)onion/[snip]/
readme_[id].txt
Quote:Hello!
Visit our Blog:
Tor Browser Links:
http://ransomxifxwc5eteopdobynonjctkxxva...ecgbqdw6qd(.)onion/
Links for normal browser:
http://ransomxifxwc5eteopdobynonjctkxxva...ecgbqdw6qd(.)onion(.)ly/
>>> Your data is stolen and encrypted.
If you don't pay the ransom, the data will be published on our TOR darknet sites. Keep in mind that once your data appears on our leak site, it could be bought by your competitors at any second, so don't hesitate for a long time. The sooner you pay the ransom, the sooner your company will be safe.
>>> If you have an external or cloud backup; what happens if you donâ t agree with us?
All countries have their own PDPL (Personal Data Protection Law) regulations. In the event that you do not agree with us, information pertaining to your companies and the data of your companyâ s customers will be published on the internet, and the respective countryâ s personal data usage authority will be informed. Moreover, confidential data related to your company will be shared with potential competitors through email and social media. You can be sure that you will incur damages far exceeding the amount we are requesting from you should you decide not to agree with us.
>>> How to contact with us?
- Install and run 'Tor Browser' from https://www.torproject.org/download/
- Go to http://davtdavm734bl4hkr3sr4dvfzpdzuzei2...uok2rxcmyd(.)onion/
- Log in using the Client ID: [snip]
>>> WARNING
DO NOT MODIFY ENCRYPTED FILES YOURSELF.
DO NOT USE THIRD PARTY SOFTWARE TO RESTORE YOUR DATA.
YOU MAY DAMAGE YOUR FILES, IT WILL RESULT IN PERMANENT DATA LOSS.
There is no patch for stupidity - Kevin Mitnick
|