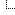Quote:A stealer log is a collection of data assembled from a victim’s device. These logs are generated by malicious software on the target device (typically running a Windows OS). Once the victim is infected, the malware then proceeds to gather personal and sensitive data to exfiltrate this back to a server being controlled by the threat actor.https://sosintel.co.uk/stealer-logs-what...d-to-know/
There are multiple varieties of stealer logs. We observe the most common to be Racoon, Redline, Titan, and Vidar, but many others can and do exist. While many strains of virus have been developed and utilised, their overall function remains consistent and the data they collect is similar across all variants. We discuss a typical log below:
Fig. 1. – An example file tree of a typical stealer log
Quote:Naming conventions for individual logs vary from stealer to stealer, but this can include such details as victim country, victim hardware id (HWID), and the date and time of capture.├─ UserInformation.txt
HWIDs are unique and are used as a security measure by Microsoft when Windows is activated. They are generated when an OS is first installed. Date and time details can be used to verify the veracity of the data.
├─ Autofills/
│ ├─ Google_[Chrome]_Default.txt
│ ├─ Google_[Chrome]_Profile1.txt
│ ├─ Microsoft_[Edge]_Default.txt
We input a lot of data into web browsers. To make this process easier, most now facilitate the auto-filling of data, saving the user considerable time. This data is stored within the browser for quick and easy recall when required. Stealer logs will routinely target this data, which can include:
Names and DOBs
Addresses
Contact details (email addresses, telephone numbers etc)
Partial credit card details
Access to this data poses a significant risk. Threat actors can and will use this gathered information to develop a profile of the victim, making it easier for them to launch successful, socially-engineered attacks.
├─ Cookies/
│ ├─ Google_[Chrome]_Default Extension.txt
│ ├─ Google_[Chrome]_Default Network.txt
│ ├─ Google_[Chrome]_Profile 1 Network.txt
│ ├─ Microsoft_[Edge]_Default Network.txt
│ ├─ Microsoft_[Edge]_Profile 1 Network.txt
│ ├─ Opera Software_Unknown Network.txt
Web browsers will also store temporary files or cookies. These will contain details about credentialed sessions on the browser, but not password information. The risk caused by the exposure of this data is that it allows a threat actor to replicate account access, potentially bypassing login details to access more sensitive information.
├─ CreditCards/
│ ├─ Microsoft_[Edge]_Default.txt
Web browsers may also save financial information, for ease of access when making online purchases. Some stealer malware variants will seek to extract this information. In this example, unredacted credit card details were saved in the Edge web browser, and extracted in full by the malware.
├─ FileGrabber/
│ ├─ Users/
│ │ ├─ Pauli/
│ │ │ ├─ Desktop/
│ │ │ │ ├─ passwords.txt
Some stealer malware variants possess the ability to extract a victim’s files. Typically, they will focus on file locations which are common across different devices and likely to hold valuable information, such as Desktop or Documents. The example above shows the victim had a text file saved on their Desktop, containing their usernames and passwords for various sites.
├─ DomainDetects.txt
This file is generated by the malware. It reads the extracted information and highlights the most common domains seen in the data. Threat actors use this analysis to identify logs of interest, i.e. those that are accessing websites and services that are of value or can be exploited further.
├─ ImportantAutofills.txt
This file is generated from parsed data from stored auto-fills. It seeks to extract data deemed most valuable to a threat actor, which can include sensitive Personally Identifiable Information (PII) and financial data.
├─ InstalledBrowsers.txt
Details all installed browsers, including version information. Identifying an old browser version could provide a threat actor opportunity to launch attacks using known exploits.
├─ InstalledSoftware.txt
Details all applications installed on a victim device, including version information. This too has value to a threat actor to identify potential vectors for exploitation.
├─ Passwords.txt
The holy grail for stealer malware. Passwords are extracted from web browsers and stored in this file, including the site name, username and cleartext password.
This file has the potential to be the most destructive for a victim and highlights the inherent risks in using native browser password storage, rather than more secure and reputable password managers.
├─ ProcessList.txt
This file contains an extract of the running processes at the time of infection. When used in combination with other gathered data, it can provide a threat actor with the opportunity to attack the device further, by utilising suitable exploits identified through this data.
├─ Screenshot.jpg
Not every stealer malware will do this, but some will take a screenshot of the victims’ screen at the point of infection. This provides some additional information regarding the victim and their habits and activities. This would have the potential to capture sensitive information if the victim is within a corporate network, or provide a threat actor with additional material for making blackmail or ransom threats.
The last file will generate details regarding the victim’s device, including IPs, hardware, location, and date
Example: screenshot
There is no patch for stupidity - Kevin Mitnick