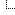Posts: 1,729
Threads: 665
Joined: Sep 2022
Reputation:
127
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV
Posts: 1,729
Threads: 665
Joined: Sep 2022
Reputation:
127
12-19-2023, 03:21 PM
(This post was last modified: 12-19-2023, 03:27 PM by 1van.
Edit Reason: Ispravljen link.
)
Uzeći u obzir da ne znamo šta je kompromitovano, ostaviću ove IP ovde u slučaju da naiđemo negde na
ukrštanje.
Izvor: SecurityTrails + DIG A.
Code:
adfs.eps.rs: aia1.eps.rs: 195.250.121.72
aia2.eps.rs: 195.252.96.114
apimgmt.eps.rs: apiportal.eps.rs: 5.183.24.60
autodiscover.eps.rs: 195.250.121.65 178.220.231.243 5.183.26.15 5.183.24.15
av.eps.rs: babel.eps.rs: 195.250.121.101
bidata.eps.rs: 195.250.121.86
bl13.eps.rs: 195.250.121.87
cip.eps.rs: 5.183.24.254
clickprd.eps.rs: 195.250.121.108
clickprd2.eps.rs: 195.250.121.108
clickprod.eps.rs: 195.250.121.108
clicktest.eps.rs: 195.250.121.108
cm-vid-all.eps.rs: 195.250.121.100
conference.eps.rs: 79.101.27.75
crl1.eps.rs: 195.250.121.72
crl2.eps.rs: 178.220.231.239
das.eps.rs: 195.250.121.61
dialin.eps.rs: dj01-vid-all.eps.rs: 195.250.121.100
dms.eps.rs: 178.220.231.237
dnsco.eps.rs: 178.220.231.39
dpp.eps.rs: 195.250.121.28
dwhtso.eps.rs: 52.166.89.108
e3.eps.rs: 195.250.121.60
ekabinet.eps.rs: 195.250.121.48
elen.eps.rs: energijacasopis.eps.rs: 195.250.121.245
epijournal.eps.rs: 5.183.24.72
epsgrupa.eps.rs: 195.250.121.62
epsict.eps.rs: 195.250.121.47
expresse.eps.rs: 195.250.121.50
expresswaye.eps.rs: 195.250.121.74
expresswaye2.eps.rs: 195.250.121.75
guest.eps.rs: 10.109.57.1 10.109.53.1
ipesoft.eps.rs: 178.220.231.235
kabinet.eps.rs: 195.250.121.45
ko-vid-all.eps.rs: 195.250.121.100
la-vid-all.eps.rs: lync.eps.rs: lyncdiscover.eps.rs: lyncpoolext2013.eps.rs: mail.eps.rs: 195.250.121.43
mail1.eps.rs: 178.220.231.242
meet.eps.rs: meteor-reklamacije.eps.rs: reklamacije.eps.rs. 195.250.121.88
mfasts.eps.rs: 195.250.121.39
msoid.eps.rs: clientconfig.microsoftonline-p.net. a.privatelink.msidentity.com. prda.aadg.msidentity.com. www.tm.a.prd.aadg.akadns.net. 40.126.31.67 20.190.159.68 20.190.159.73 40.126.31.69 20.190.159.71 20.190.159.75 20.190.159.23 20.190.159.4
mtoken.eps.rs: 195.250.121.108
ns1.eps.rs: 195.250.121.25
ns2.eps.rs: 178.220.231.39
ns3.eps.rs: 5.183.24.53
ns4.eps.rs: 5.183.26.53
ns5.eps.rs: 5.183.24.54
ocsp1.eps.rs: 195.250.121.72
ocsp2.eps.rs: 195.252.96.114
owa.eps.rs: 5.183.26.15 5.183.24.15 195.250.121.65 178.220.231.243
pki.eps.rs: 195.250.121.41
portal.eps.rs: 5.183.24.60
posta.eps.rs: 195.250.121.31
posta1.eps.rs: 195.250.121.26
posta2.eps.rs: 212.200.144.109
posta3.eps.rs: 212.200.144.110
prijava.eps.rs: pristup.eps.rs: 178.220.231.241
private.eps.rs: 195.250.121.27
prognoza.eps.rs: 195.250.121.70
protis.eps.rs: 195.250.121.19
rameses.eps.rs: 195.250.121.25
razmena.eps.rs: 195.250.121.59
reklamacije.eps.rs: 195.250.121.88
reorg.eps.rs: 195.250.121.46
rwe.eps.rs: 195.250.121.27
sapr.eps.rs: 195.250.121.52
sbgawcg01.eps.rs: 195.250.121.83
sbgawds01.eps.rs: 195.250.121.80
sbgawmp01.eps.rs: 195.250.121.82
sbgawseg01.eps.rs: 195.250.121.81
secure.eps.rs: 195.250.121.29
see.eps.rs: 178.220.231.41
sip.eps.rs: sp2013owa.eps.rs: 195.250.121.19
spoee-field.eps.rs: 178.220.231.237
spoeetest.eps.rs: 195.250.121.108
tenderroom.eps.rs: 195.250.121.62
tent-vid-all.eps.rs: 195.250.121.100
vcse.eps.rs: vpn.eps.rs: 178.220.231.240
vr-vid-all.eps.rs: vr01-vid-all.eps.rs: 195.250.121.100
vr02-vid-all.eps.rs: wac.eps.rs: web.eps.rs: 195.250.121.99
webconf.eps.rs: wifi.eps.rs: 1.1.1.1
www.eps.rs: 20.224.189.238
www.portal.eps.rs: 5.183.24.60
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV
Posts: 1,729
Threads: 665
Joined: Sep 2022
Reputation:
127
Da nije "kripto" tipa ustvari ovaj: trojan-ransom.win32.Crypmod.gen ?
Izvor:
https://cybermap.kaspersky.com/stats#cou...V&period=w
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV
Posts: 1,729
Threads: 665
Joined: Sep 2022
Reputation:
127
Dobili smo neproverene informacije da se radi o Qilin (Agenda) Ransomware.
Code:
Ransom Demanding Message:
[random_string]-RECOVER-README.txt
Detection Names:
Avast: Win64:Trojan-gen
Sophos: Mal/Generic-S
Emsisoft: Trojan.Ransom.Babuk.F (B)
Kaspersky: Trojan.Win32.DelShad.ivd
Malwarebytes: Generic.Malware/Suspicious
Microsoft: Ransom:Win32/Babuk.SIB!MTB
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV
Posts: 1,729
Threads: 665
Joined: Sep 2022
Reputation:
127
Ko je poslao ovu poruku?
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV