Posts: 1,728
Threads: 664
Joined: Sep 2022
Reputation:
126
Quote:On 5 October 2023, a major global investigation – the “Predator Files” – was published exposing the proliferation of surveillance technologies around the world and the failure of governments and the European Union (EU) to properly regulate the industry. The Security Lab at Amnesty International is a technical partner in the “Predator Files”, a project coordinated by the European Investigative Collaborations (EIC) media network into the Intellexa alliance, the makers and marketers of the Predator spyware. As part of this collaboration, the Security Lab has reviewed technical documentation, marketing material and other records obtained by Der Spiegel and Mediapart – who are part of EIC – which shed light on the ecosystem of surveillance products offered by the Intellexa alliance.
The Intellexa alliance is an evolving group of companies and brands that have been involved in developing and marketing a wide range of surveillance products including advanced spyware, mass surveillance platforms, and tactical systems for targeting and intercepting nearby devices. The corporate entities of the alliance span various jurisdictions, both within and outside the EU. The exact nature of links between these companies is shrouded in secrecy as corporate entities, and the structures between them, are constantly morphing, renaming, rebranding, and evolving.
In the same vein, the products marketed by Intellexa have been rebranded and renamed numerous times, as various Intellexa alliance entities have worked together to combine product development and marketing activities. This report provides an overview of the distinct products and “attack vectors” offered by this surveillance alliance, including a product glossary to help clarify the analysis where multiple product names were used to describe the same product line over time. This report does not endeavour to describe every product in exhaustive detail, but rather to provide an overview of known or significant products. The goal of this research is also to provide an understanding of the potential impact of the described attack techniques, without making a judgement on the effectiveness of individual products, since marketing material can often overstate the effectiveness of commercial products.
Technical specifications and marketing material from surveillance vendors is often kept secret. The resulting information asymmetry prevents defenders in the cybersecurity industry and at-risk civil society groups from understanding the full scope of threats that they face. The aim of this research is to provide concrete information about surveillance capabilities available from this one vendor in the commercial surveillance market. We hope that this report can be a resource for the cybersecurity community and major mobile device and technology vendors. Our recommendations section outlines possible mitigations and detections which can help protect potential civil society targets and the wider internet ecosystem from some of the attack vectors described here.
Details: https://securitylab.amnesty.org/latest/2...-products/
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV
Posts: 1,728
Threads: 664
Joined: Sep 2022
Reputation:
126
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV
Posts: 1,728
Threads: 664
Joined: Sep 2022
Reputation:
126
11-28-2023, 04:53 PM
(This post was last modified: 11-28-2023, 04:58 PM by 1van.
Edit Reason: Ubačeni detalji.
)
Izvor: https://www.slobodnaevropa.org/a/srbija-...03352.html
Quote:"Vidimo da su napadi bili vrlo slični vremenski, otprilike jedan minut razlike između napada. Dve odvojene osobe, dva odvojena Ajfona (iPhone)", rekla je za RSE Natalia Krapiva iz organizacije Access Now, pojašnjavajući nalaze.
"Mi nismo bili u mogućnosti da napad pripišemo određenoj vrsti špijunskog softvera, ali napad izgleda prilično konzistentno sa špijunskim softverom 'Pegasus', na osnovu forenzičkih artefakata koje smo otkrili na telefonima", izjavio je za RSE Bill Marczak iz organizacije Citizen Lab.
Quote:NSO grupa, kako dodaje, ne prodaje ovu vrstu softvera pojedincima, već nosioci licence moraju biti državne institucije.
Marczak dalje pojašnjava da je njegova organizacija istraživala lokacije servera sa kojih se upravlja hakerskim softverima.
"Možemo videti gde su operateri koji imaju Pegasus na osnovu lokacija servera", kaže Marczak, i dodaje da su jedan server ranije "povezali sa Srbijom".
Marczak zaključuje da "osim posrednih dokaza", digitalna forenzička analiza nije našla direktnu vezu između Vlade Srbije i pokušaja hakerskog napada na telefone predstavnika civilnog društva.
Quote:Istraživanje je, kako navodi, pokazalo da je napadač u telefone "ušao" preko aplikacije HomeKit koju imaju svi napredniji Apple telefoni.
"To je neka vrsta aplikacije za kontrolu pametnih uređaja u kući. Čak i ako vi kao korisnik iPhone-a niste ušli u tu aplikaciju, podesili bilo šta, koristili je, ona je i dalje instalirana u vašem telefonu i radi", dodaje Marzak.
Prema njegovim rečima, bezbednosne greške u toj aplikaciji su iskorišćene za pokušaj napada.
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV
Posts: 58
Threads: 31
Joined: Sep 2022
Reputation:
54
11-29-2023, 08:46 PM
(This post was last modified: 11-29-2023, 08:57 PM by Petar.)
Koliko je meni jasno iz ovoga jeste da NSO razvija Zero-Click napade na osnovu Zero-Day propusta koje pronadju.
To znaci da zrtva ne treba da uradi nista da bi napad bio uspesan, a napad obicno zapocinje kada napadac posalje specijalno dizajniranu SMS, email, ili neku drugu instant-messaging poruku.
U prevodu NSO zna za propust za koji ni Apple ne zna i ima nacina da ga upotrebi na metu (korisnika iPhone-a) bez da ona ista treba da uradi/klikne.
Preporuka je da se omoguci Apple-ov LockDown mod zastite kako bi bar bili obavesteni o sumnjivim blokiranim aktivnostima na vasem iPhone-u.
Triple Threat: NSO Group’s Pegasus Spyware Returns in 2022 with a Trio of iOS 15 and iOS 16 Zero-Click Exploit Chains - The Citizen Lab
Kako se u iznad navedenom izvestaju CitizenLab-a navodi, nije uoceno da su napadi bili uspesni na uredjaje koji su imali LockDown mod upaljen.
Postoji i softver koji se slobodno moze koristiti za forenziku telefona MVT.
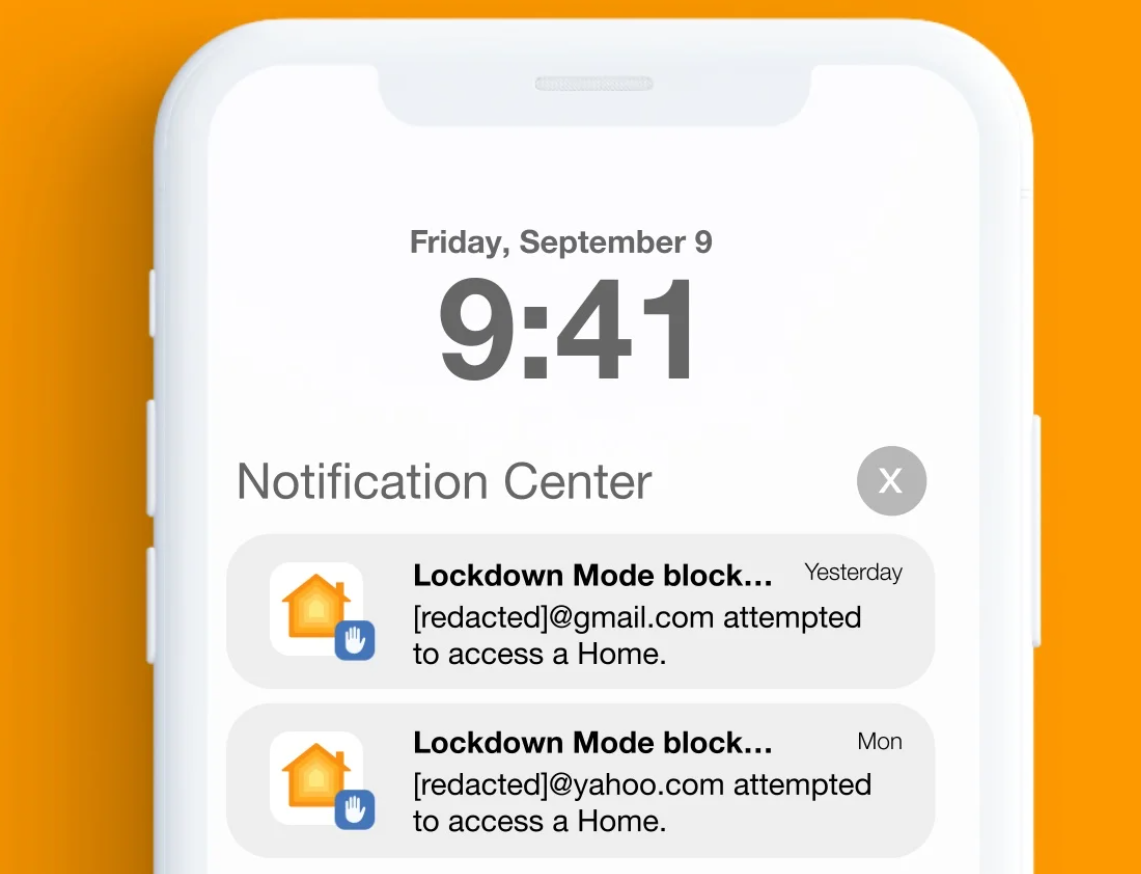
Ako ste meta od velikog znacaja i mislite da ste takodje targetirani po obavestenjima od Apple Threat Notification ili notifikaciji od LockDown-a na iPhone-u, moze te se obratiti:
Lista jos korisnih kontakata: Tool: Find Emergency Resources - Consumer Reports Security Planner
Posts: 58
Threads: 31
Joined: Sep 2022
Reputation:
54
Posts: 1,728
Threads: 664
Joined: Sep 2022
Reputation:
126
11-30-2023, 07:38 AM
(This post was last modified: 11-30-2023, 07:43 AM by 1van.
Edit Reason: Ispravljen link.
)
Da dodamo i ove: danas[.]bid, svetovid[.]bid, kormoran[.]bid i bumabar[.]bid
Quote:BIRN je pronašao još nekoliko sumnjivih domena sa karakterističnim završetkom “.bid”, koji su izgleda bili rezervisani za žrtve u Srbiji. Pretpostavlja se da su i domeni “danas.bid”, “svetovid.bid” , “kormoran.bid” i “bumabara.bid” mogli biti zaraženi virusom. Posebno je interesantan domen “svetovid.bid” za koji postoji više indikatora da se radi o spajver programu, odnosno programu za nadzor.
Ono što je karakteristično za sve “.bid” domene je što su registrovani u Srbiji na dan 23. maj 2020. godine, izuzev domena “politika.bid” koji je kreiran dan pre, 22. maja 2020. godine, a kao zemlja registracije tog domena navode se Sjedinjene Američke Države.
Izvor: https://about.fb.com/wp-content/uploads/...dustry.pdf
Izvor: https://birn.rs/izraelski-softveri-za-sp...predatora/
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV
Posts: 1,728
Threads: 664
Joined: Sep 2022
Reputation:
126
11-30-2023, 07:42 AM
(This post was last modified: 11-30-2023, 07:44 AM by 1van.
Edit Reason: Ispravljen link.
)
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV
Posts: 1,728
Threads: 664
Joined: Sep 2022
Reputation:
126
“If you think you are too small to make a difference, try sleeping with a mosquito.” - Dalai Lama XIV
|